Firewall
A firewall is a network security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules. A firewall typically establishes a barrier between a trusted network and an untrusted network, such as the Internet. In other words, a firewall exists between your computer and the network, and determines which resources on your computer remote users on the network can access. … A properly configured firewall can greatly increase the security of your system.
Benefits of Firewall Security:
Traffic Control: A firewall monitors all of the traffic entering your computer or network.
Default Rules: A fully configurable list of default rules which can be applied to all traffic.
Blocks Trojans: A firewall helps block Trojan Horses
Port Access: Granular control to tailor rules with options like allowing all traffic to your website or ensuring only you and your developer can access SSH ports or RDP.
Stops Hackers: Having a firewall keeps hackers out of your network.
Additional Server Resources: Access to additional server resources that would otherwise be utilized. You can even disable the software firewalls from your server and rely completely on the Hardware Firewall, freeing up valuable memory and processor for the functions and services that your business needs to continue being successful.
Firewall Configuration
Reviewing firewall security will check the firewall configuration, firmware updates, and security configuration. It is mandatory that all firms which communicate through a network should undergo a firewall security review. Most of the standards like PCI DSS, ISO 27001, SOX and HIPAA require firewall security review.
DSI Dubai is experienced in installation and configuration of various firewalls and VPN solutions. Realizing the fact that how important the firewall configuration to an enterprise is, we provide firewall security with advanced performance configuration and trouble shooting. Incorrect configuration can leave any network exposed to data theft, malware attacks and other types of intrusions. Firewall security serves as a line of defense to combat a serious range of damaging malware and other intrusions. Prevention mechanism is dependent on the type of firewall in use and how it is being configured. Therefore, more than just securing your network it is important to get the firewall system configured properly.
Types of Firewall
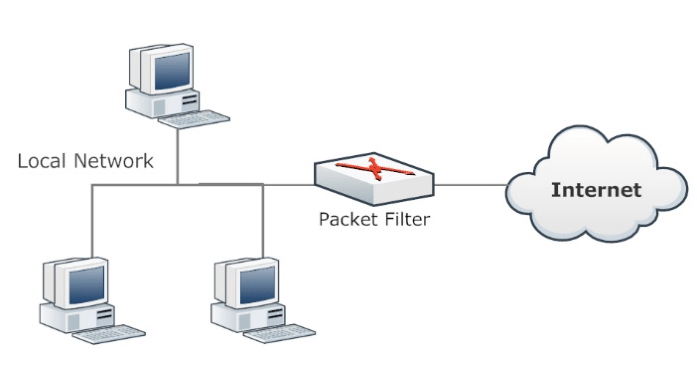
Packet-filtering firewalls
These are the most basic and oldest type of firewalls that inspect packets transferred between computers. The firewall maintains an access control list which dictates what packets will be looked at and what action should be applied, if any, with the default action set to silent discard.
Circuit-level gateways
Circuit-level gateways work by verifying the transmission control protocol (TCP) handshake. This TCP handshake check is designed to make sure that the session the packet is from is legitimate.

Stateful inspection firewalls
These firewalls combine both packet inspection technology and TCP handshake verification to create a level of protection greater than either of the previous two architectures could provide alone.
Application-level gateways
These operate at the application layer to filter incoming traffic between your network and the traffic source. Rather than letting traffic connect directly, the proxy firewall first establishes a connection to the source of the traffic and inspects the incoming data packet.
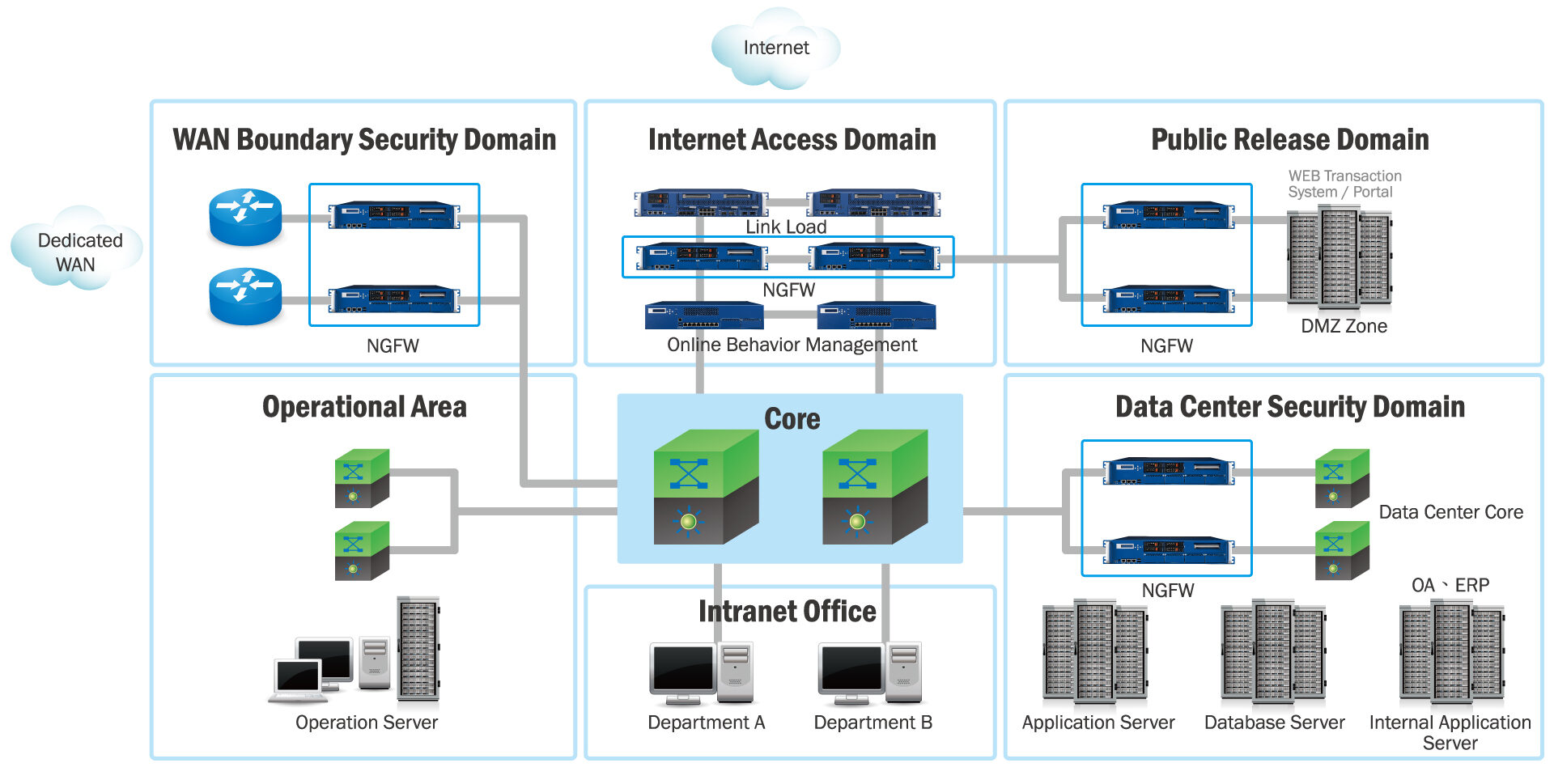
Next-gen firewalls
Next-gen firewall include deep-packet inspection (checking the actual contents of the data packet), TCP handshake checks, and surface-level packet inspection. It may include other technologies as well, such as intrusion prevention systems (IPSs) that work to automatically stop attacks against your network.
Software firewalls
Software firewalls are installed on your computer (like any software) and you can customize it, allowing you some control over its function and protection features. A software firewall will protect your computer from outside attempts to control or gain access your computer, and, depending on your choice of software firewall, it could also provide protection against the most common Trojan programs or e-mail worms.
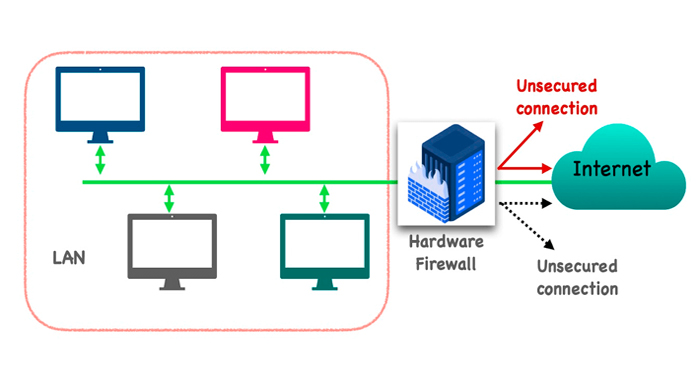
Hardware firewalls
Hardware firewalls use a physical appliance that acts in a manner similar to a traffic router to intercept data packets and traffic requests before they’re connected to the network’s servers. Physical appliance-based firewalls like this excel at perimeter security by making sure malicious traffic from outside the network is intercepted before the company’s network endpoints are exposed to risk.
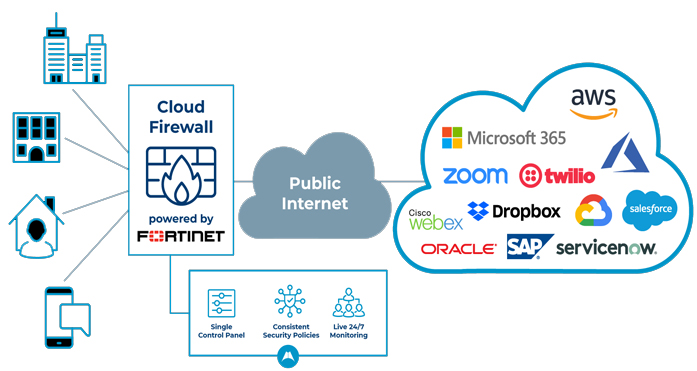
Cloud firewalls
Whenever a cloud solution is used to deliver a firewall, it can be called a cloud firewall. A cloud server is often used in a proxy firewall setup (though the proxy doesn’t necessarily have to be on the cloud, it frequently is). The big benefit of having cloud-based firewalls is that they are very easy to scale with your organization. Cloud firewalls, like hardware firewalls, excel at perimeter security.